Azure AZ-900 notes
Intro
Notes of azure az-900 training
Tree:
- Azure AD tenant
- Management groups
- Suscriptions
- Resource Groups
- Resources
- Resource Groups
- Suscriptions
- Management groups
Describe core Azure services
Each service provides different options depending on your requirements. Some of the most prominent services are:
- Azure Virtual Machines
- Azure Container Instances
- Azure App Service
- Azure Functions (or serverless computing)
App Service
With App Service, you can host most common app service styles like:
- Web apps
- API apps
- WebJobs
- Mobile apps
Containerazation
Manage containers
Containers are managed through a container orchestrator, which can start, stop, and scale out application instances as needed. There are two ways to manage both Docker and Microsoft-based containers in Azure: Azure Container Instances and Azure Kubernetes Service (AKS).
Explore Azure networking services
Azure virtual networking
Azure virtual networks provide the following key networking capabilities:
- Isolation and segmentation
- Internet communications
- Communicate between Azure resources
- Communicate with on-premises resources
- Route network traffic
- Filter network traffic
- Connect virtual networks
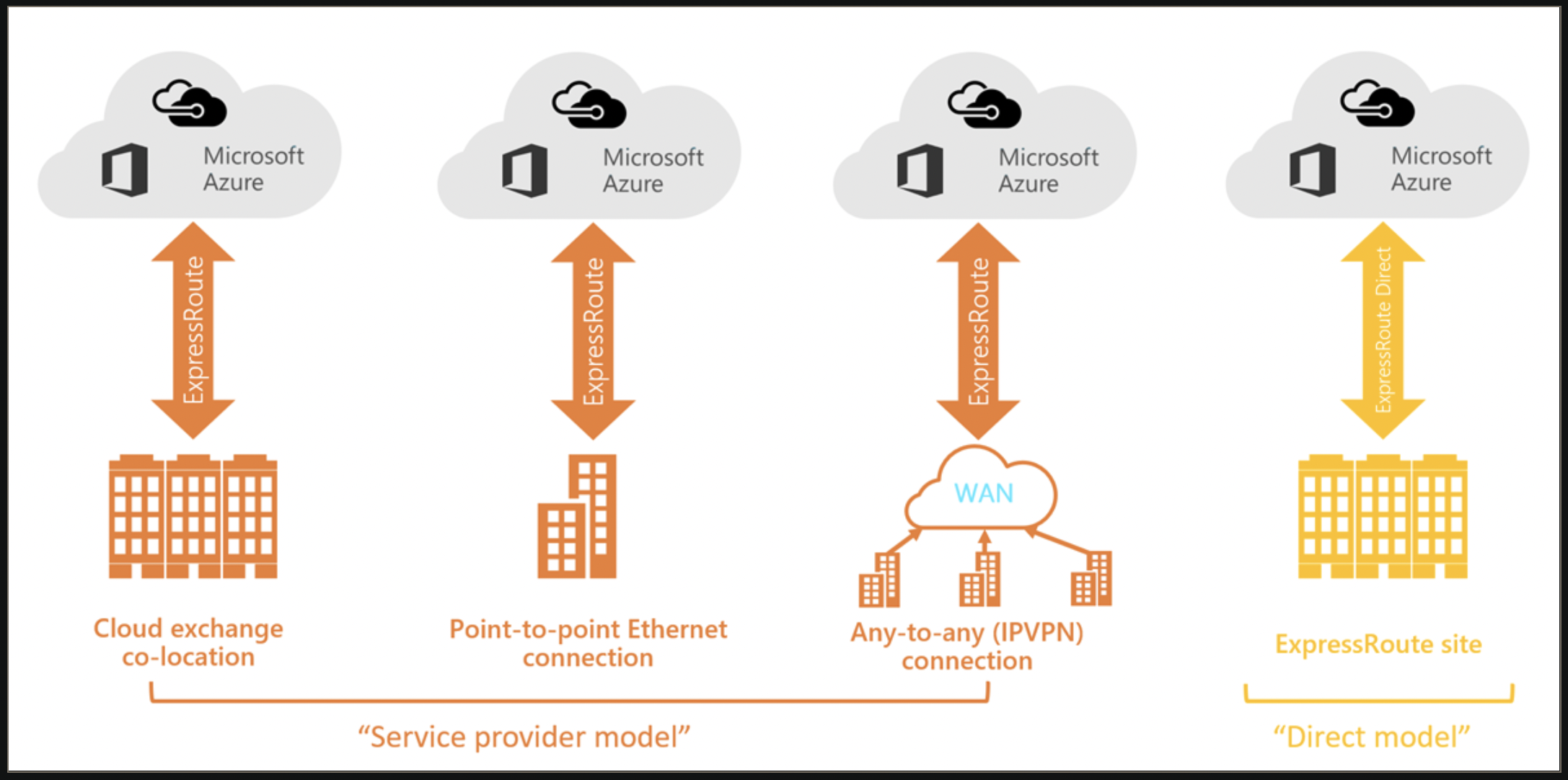
Azure Express route
Is used to connect on-premises infrastructure with cloud services of azure. The connection is not encrypted.
- It has the following connectivity models:
- CloudExchange colocation
- Point-to-point Ethernet connection
- Any-to-any connection
Directly from ExpressRoute sites
Explore Azure storage services
- Azure Blob Storage
- Azure Disk Storage
- Azure Files Storage
Azure Blob Access tiers
Notes
nrsa: non-revenue services ssm: self service FOS: flight operation system
Explore Azure databases and analytics services
Azure SQL Database
Azure SQL Managed Instance
Explore big data and analytics
- Azure Synapse Analytics antes sql data warehouse,
- Azure HDInsight opensource
- Azure Databricks se puede usar con python, R, java y sql
- Azure Data Lake Analytics. para uso on-demand.
Protect against security threats on Azure
Secure network connectivity on azure
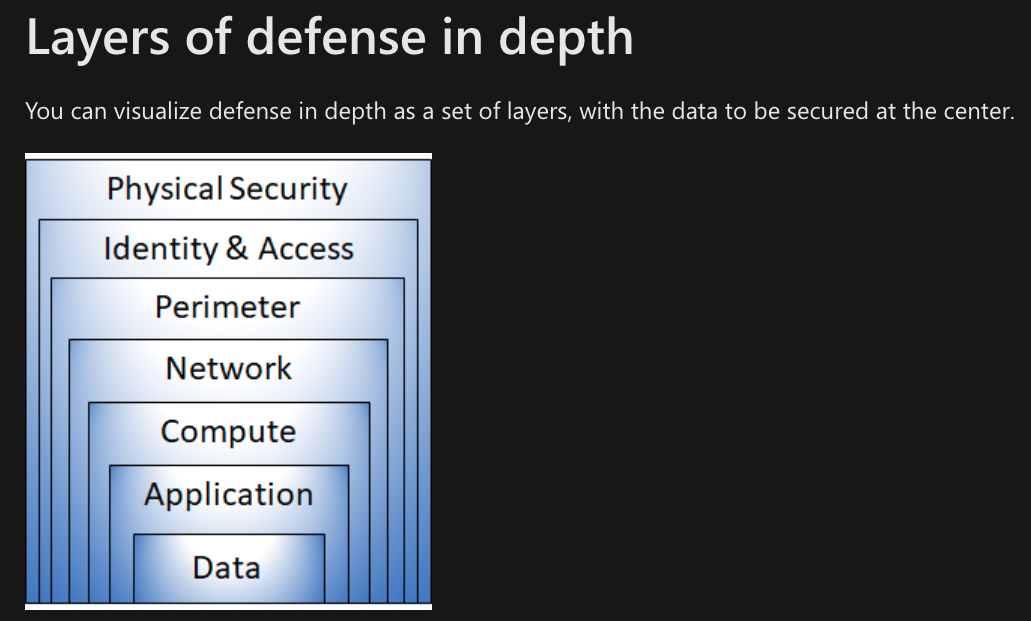
What is defense in depth?
- The objective of defense in depth is to protect information and prevent it from being stolen.
- A defense-in-depth strategy uses a series of mechanisms to slow the advance of an attack that aims at acquiring unauthorized access to data.
Security posture
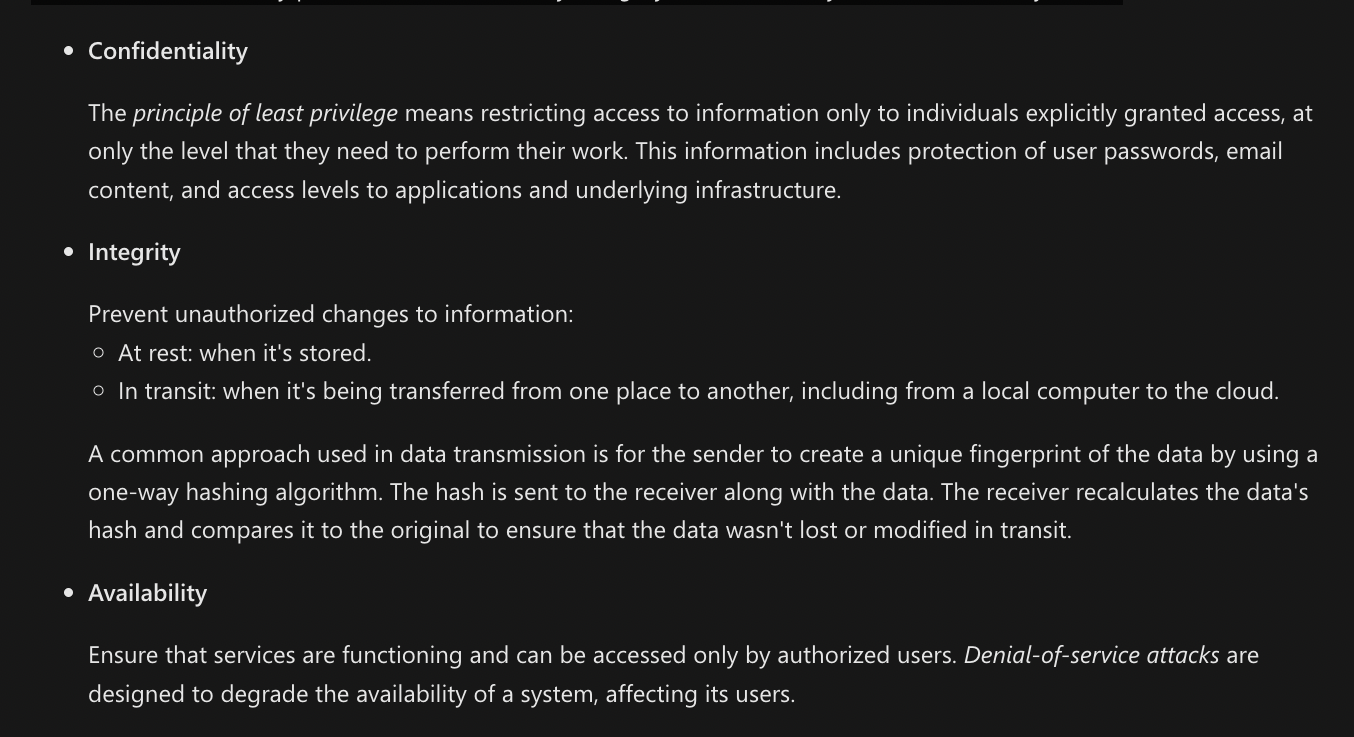
The common principles used to define a security posture are confidentiality, integrity, and availability, known collectively as CIA.
Protect virtual networks by using Azure Firewall
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.
You typically deploy Azure Firewall on a central virtual network to control general network access.
With Azure Firewall, you can configure:
- Application rules that define fully qualified domain names (FQDNs) that can be accessed from a subnet.
- Network rules that define source address, protocol, destination port, and destination address.
- Network Address Translation (NAT) rules that define destination IP addresses and ports to translate inbound requests.
Protect from DDoS attacks by using Azure DDoS Protection
A distributed denial of service attack attempts to overwhelm and exhaust an application’s resources, making the application slow or unresponsive to legitimate users. DDoS attacks can target any resource that’s publicly reachable through the internet, including websites.
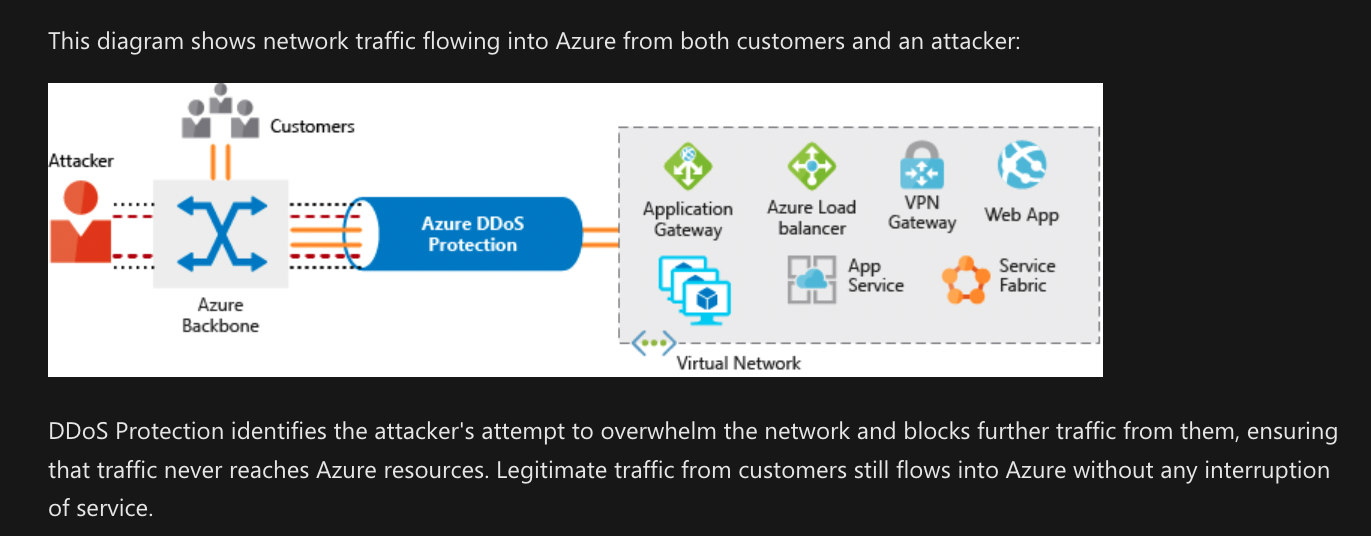

Filter network traffic by using network security groups
A network security group enables you to filter network traffic to and from Azure resources within an Azure virtual network. You can think of NSGs like an internal firewall.
- Use Azure DDoS Protection to filter large-scale attacks before they can cause a denial of service for users.
- Use perimeter firewalls with Azure Firewall to identify and alert on malicious attacks against your network.
Secure access to your applications by using Azure identity services
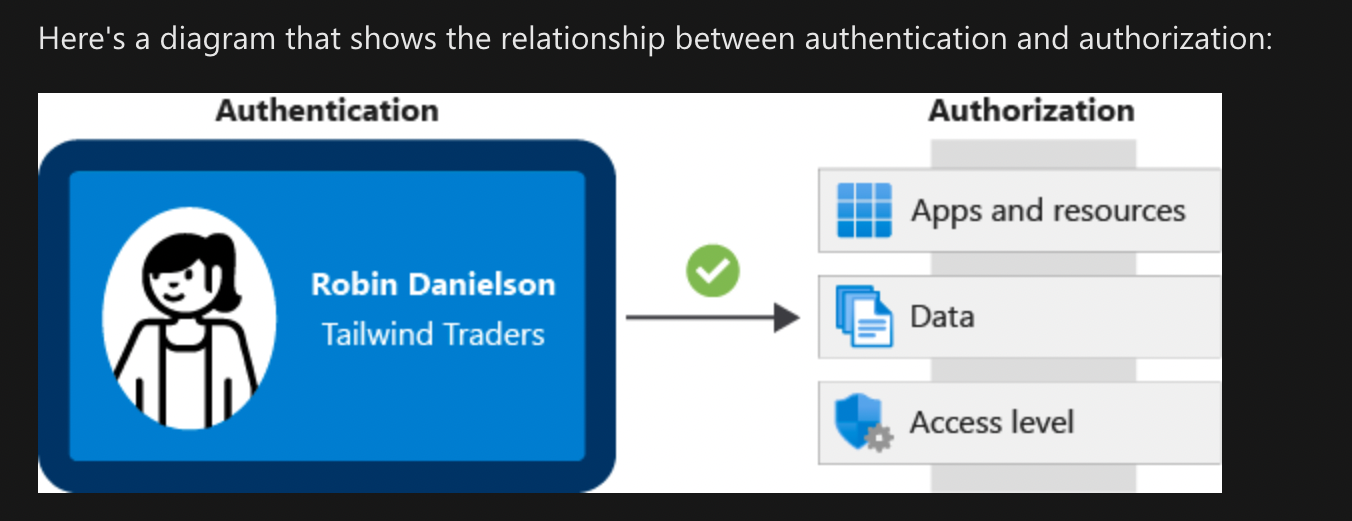
Compare Authentication and Authorization
What is Authentication?
It establishes whether the user is who they say they are.
What is Authorization?
Authentication establishes the user’s identity, but authorization is the process of establishing what level of access an authenticated person or service has. It specifies what data they’re allowed to access and what they can do with it.
How are Authentication and Authorization related?
What services does Azure AD provide?
- Authentication This includes verifying identity to access applications and resources. It also includes providing functionality such as self-service password reset, multifactor authentication, a custom list of banned passwords, and smart lockout services.
- Single sign-on SSO enables you to remember only one username and one password to access multiple applications.
- Application management
- Device management
What’s multifactor authentication?
Multifactor authentication is a process where a user is prompted during the sign-in process for an additional form of identification. Examples include a code on their mobile phone or a fingerprint scan.
Multifactor authentication provides additional security for your identities by requiring two or more elements to fully authenticate.
These elements fall into three categories:
- Something the user knows This might be an email address and password.
- Something the user has This might be a code that’s sent to the user’s mobile phone.
- Something the user is This is typically some sort of biometric property, such as a fingerprint or face scan that’s used on many mobile devices.
Build a cloud governance strategy on Azure
The term governance describes the general process of establishing rules and policies and ensuring that those rules and policies are enforced.
Control access to cloud resources by using Azure role-based access control
Role-based access control is applied to a scope, which is a resource or set of resources that this access applies to.
Resource Manager is a management service that provides a way to organize and secure your cloud resources.
Who does Azure RBAC (role-based access control) apply to?
- individuals (users or resources)
- groups
- special identity types such as “service principals” and “managed indentities”
To manage the RBAC you can go to the IAM section on the Azure portal.
Prevent accidental changes by using resource locks
A resource lock prevents resources from being accidentally deleted or changed.
What levels of locking are available?
- CanNotDelete: user can view and modify the resource.
- ReadOnly: user can only view the resource, he can’t delete nor modify.
Resource locks apply regardless of RBAC permissions. Even if you’re an owner of the resource, you must still remove the lock before you can perform the blocked activity.
Combine resource lock with Azure Blueprints
What if a cloud administrator accidentally deletes a resource lock? If the resource lock is removed, its associated resources can be changed or deleted.
To make the protection process more robust, you can combine resource locks with Azure Blueprints. Azure Blueprints enables you to define the set of standard Azure resources that your organization requires. For example, you can define a blueprint that specifies that a certain resource lock must exist. Azure Blueprints can automatically replace the resource lock if that lock is removed.
Organize your resources by using tags
Interestingly we can use Azure DevOps and process resources with certain tag. We can also use tags for creating cost managament, security and governance and regulatory compliance.
How do I manage resource tags?
- PowerShell
- Azure CLI
- Azure Resource Manager templates
- REST API or
- Azure Portal
You can also use Azure Policy to enforce tagging rules and conventions.
A tag consist of a name and value.
Azure Policy
Website: Azure Policy - Getting started
Control and audit your resources by using Azure Policy.
Azure Policy enables you to define both individual policies and groups of related policies, known as initiatives. Azure Policy evaluates your resources and highlights resources that aren’t compliant with the policies you’ve created. Azure Policy can also prevent noncompliant resources from being created.
A policiy consists of a
- definition
- resource of which the definition will be applied.